Build a Modern Cybersecurity Foundation with a Proven Zero Trust Security Model
Zero Trust Strategy Workshop by BTA
The Zero Trust Strategy Workshop by BTA is a hands-on consulting service designed to help IT and security leaders define, assess, and implement a Zero Trust architecture that protects every identity, workload, and device across the enterprise.From organizations just beginning their Zero Trust implementation to teams refining their access control and segmentation strategy, this workshop delivers practical, business-aligned insights to strengthen your cybersecurity posture.
What You’ll Gain
Defining & Implementing Zero Trust
- A clear understanding of the Zero Trust security model and its core principles
- A mapped alignment of business and technical requirements to a Zero Trust framework
- A segmentation strategy tailored to your organization’s structure
- An assessment of your current security architecture and defined trust boundaries
- A strategy for authentication, visibility, and continuous verification
- A Risk Profile Discussion outlining key vulnerabilities and priorities


Zero Trust Architecture Best Practices
- Guidance on Zero Trust Network Access (ZTNA) concepts and deployment models
- Recommendations for least privilege access strategies and enforcement
- A micro-segmentation and policy deployment roadmap
- Evaluation of risk profiles, change management, and CVE reporting practices
- Insights to strengthen management reporting and compliance alignment
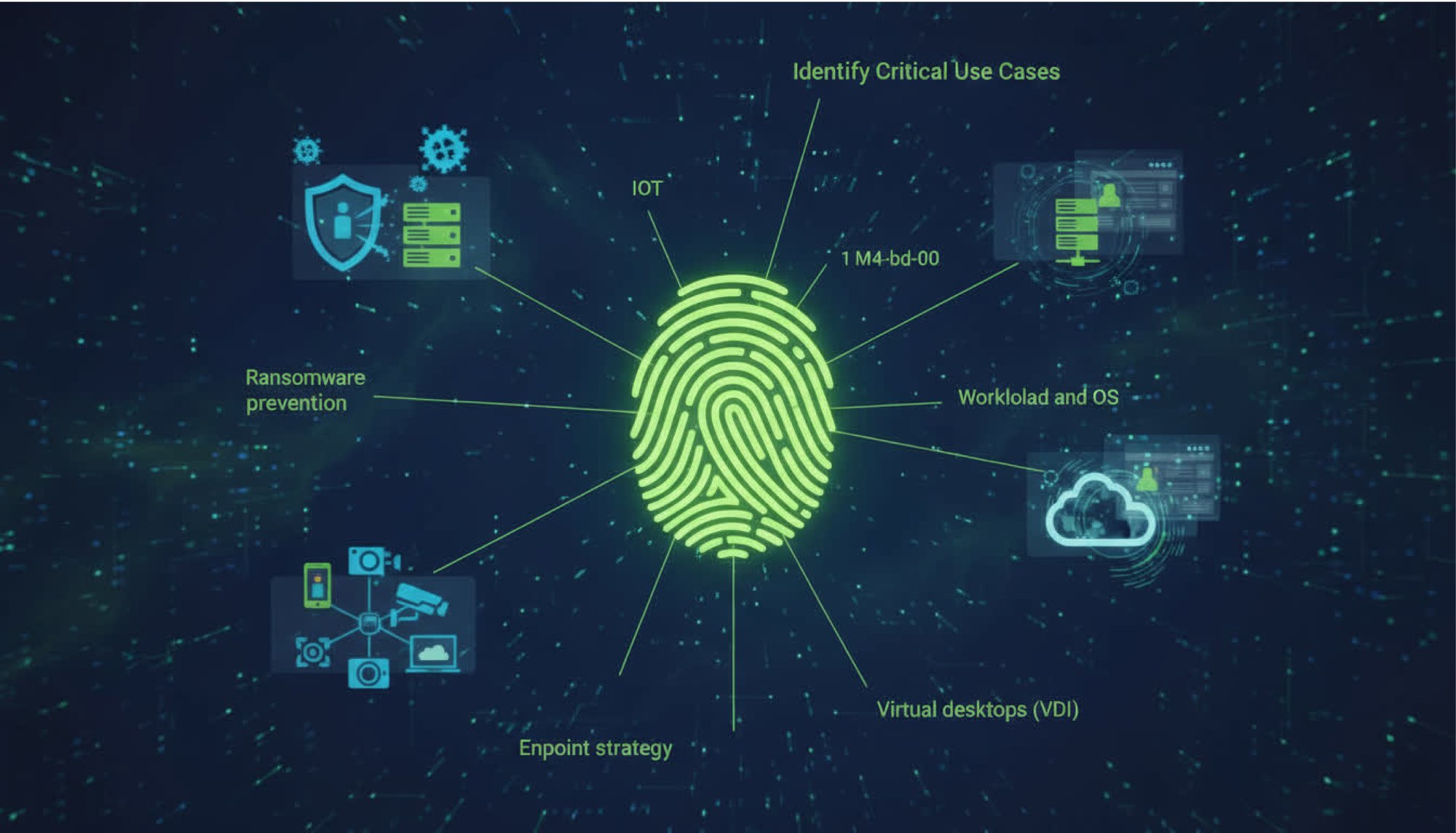
Identify Critical Use Cases
- Strategies for ransomware prevention through Zero Trust controls
- Protection plans for workloads, operating systems (OS), and virtual desktops (VDI)
- A defined endpoint security and IoT access approach
- Evaluation of cloud workload protection and identity access management (IAM) solutions
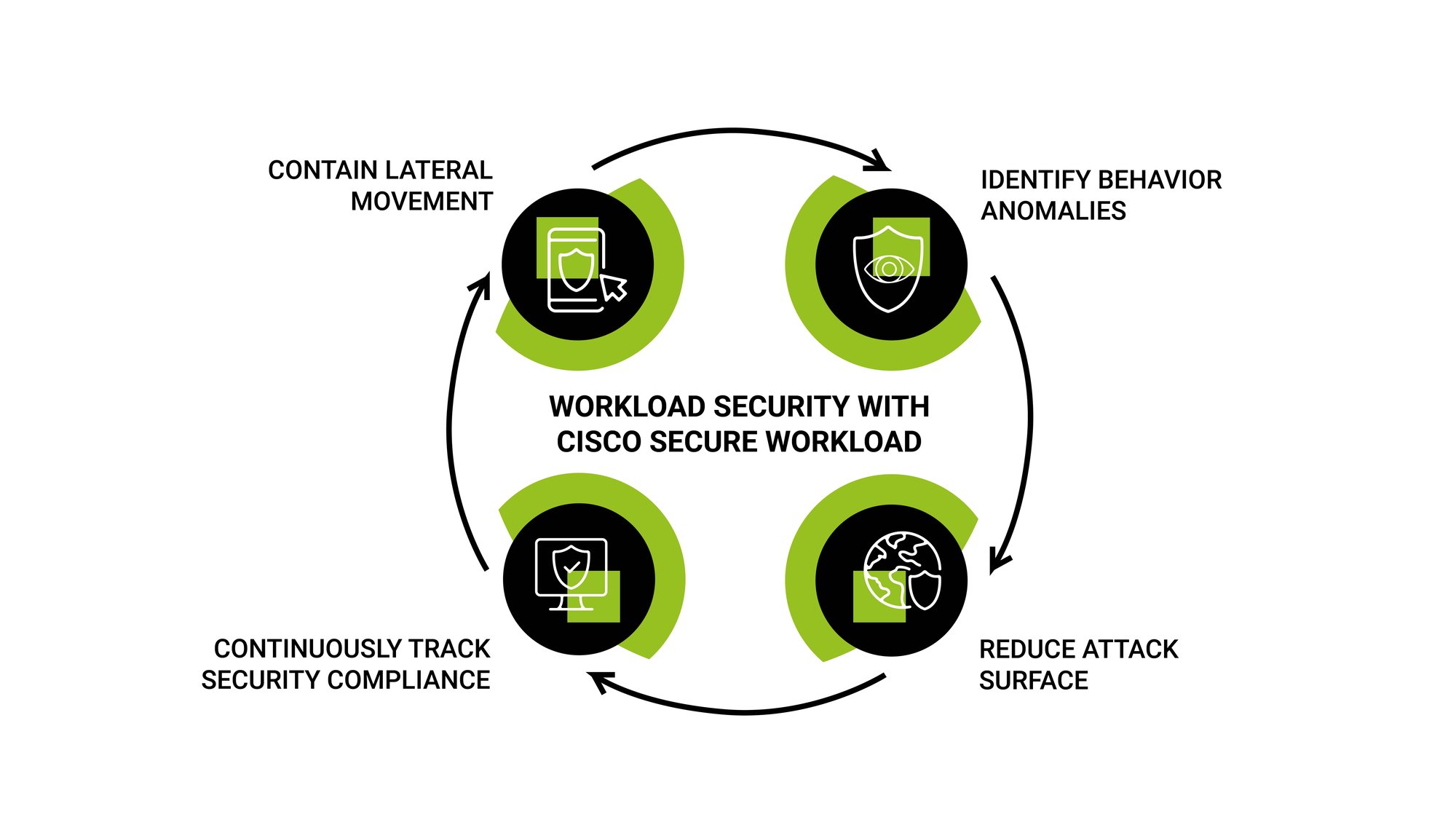
BTA Read-Out & Recommendations
- A full ROI and business impact analysis
- Tailored tool and solution recommendations based on your environment
- Guidance on managed services for long-term Zero Trust maturity
Why Choose the BTA Zero Trust Workshop
- Led by BTA cybersecurity architects with deep expertise in Zero Trust strategy and deployment
- Built on proven Zero Trust methodologies derived from real-world implementations
- Designed to align security, IT, and business goals through measurable, scalable outcomes
- Delivers an actionable roadmap tailored to your environment and maturity level

Get Started with BTA
Take the next step toward a secure, resilient, and identity-centric enterprise.
Request your Zero Trust Strategy Workshop today and start building your Zero Trust roadmap with confidence.
.png?width=225&height=90&name=Logos%20BTA%20(500%20x%20200%20px).png)